
Preparing for the Microsoft MD-101 exam needs to be systematic and targeted. To this end, Pass4itSure has updated the MD-101 dumps 2023 https://www.pass4itsure.com/md-101.html (three product formats PDF, Software, Software + PDF to accelerate Microsoft MD-101 exam preparation) in April 2023, providing systematic and targeted exam study materials to help you prepare.
Why does preparing for the MD-101 exam need to be systematic and targeted?
You definitely have this doubt. Read on.
Preparing for the MD-101 exam needs to be systematic and targeted, as it is a relatively complex and broad exam that covers multiple topics and skills.
- Systematic preparation can help candidates allocate time and energy reasonably, fully grasp the knowledge points and skills required by the exam, and reduce the risk of failing the exam.
- At the same time, targeted preparation can select learning resources and formulate study plans according to the actual situation and needs of candidates themselves, so as to improve the efficiency and performance of test preparation.
You may also ask, how to prepare for the MD-101 exam systematically and in a targeted manner.
The following points need to be done:
Create a test preparation plan:
Make a preparation plan based on the content of the Microsoft MD-101 exam and your own schedule.
Consider the importance and difficulty of each topic and step by step through the exam preparation goals.
Selection of learning resources:
Choose from authoritative learning resources such as official guides, reference books, or Pass4itSure MD-101 dumps and combine them with hands-on exercises.
Hands-on:
Do as much hands-on as you can to acquire relevant skills and deepen your understanding.
Conduct a mock test:
During the preparation process, take a mock test to test the knowledge and skills you have learned. Mock tests can help you understand the format and difficulty of the exam, and identify your weaknesses to improve your preparation further.
Continuous Learning:
Constantly update your knowledge and follow the latest technologies and trends to stay competitive and flexible.
The updated dumps are used to pass the Microsoft MD-101 exam
We recognize how difficult the Microsoft MD-101 certification exam can be. Therefore, it is important to pick how you prepare to ensure that you are using the best learning resources to prepare for the exam. Pass4itSure’s updated MD-101 dumps are the best way to do it.
Get ahead and take a look at the free questions below.
MD-101 free dumps exam questions online (Updated April 2023)
Question 1:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 8.1.
Computer1 has apps that are compatible with Windows 10. You need to perform a Windows 10 in-place upgrade on Computer1.
Solution: You copy the Windows 10 installation media to a network share. You start Computer1 from Windows PE (WinPE), and then you run setup.exe from the network share. Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/windows/deployment/windows-deployment-scenarios-and-tools
Question 2:
HOTSPOT
You have 200 computers that run Windows 10. The computers are joined to Microsoft Azure Active Directory (Azure AD) and enrolled in Microsoft Intune.
You need to configure an Intune device configuration profile to meet the following requirements:
1. Prevent Microsoft Office applications from launching child processes.
2. Block users from transferring files over FTP.
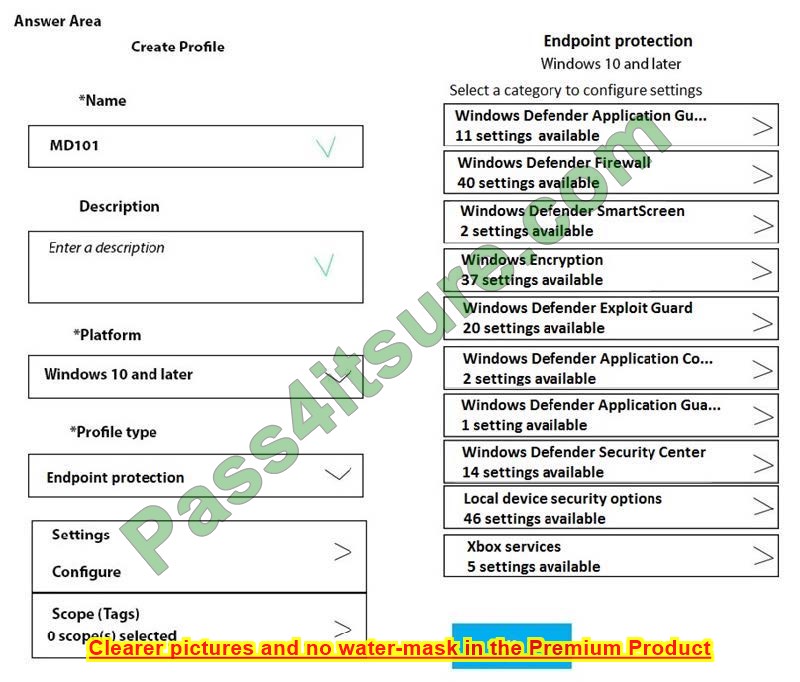
Which two settings should you configure in Endpoint protection? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
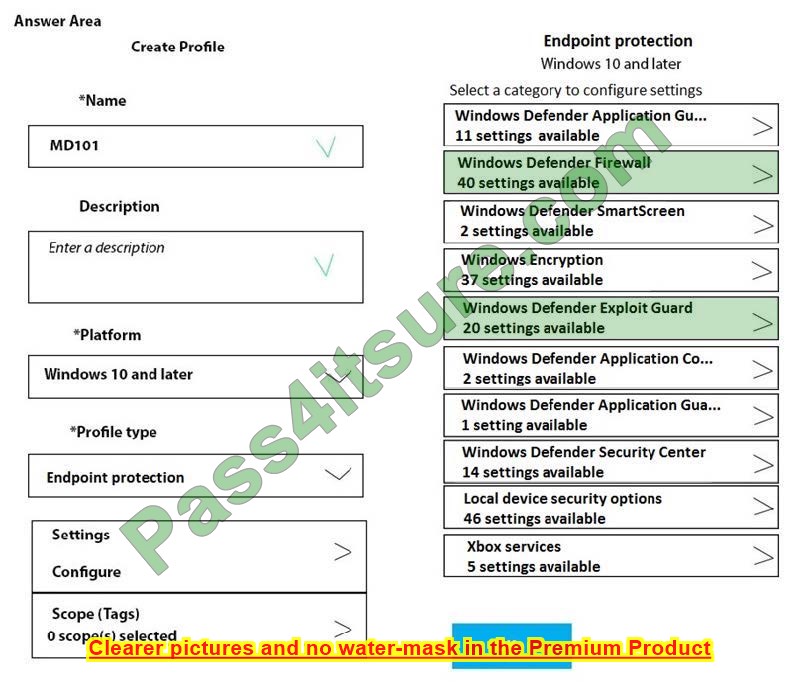
Box 1: Microsoft Defender Firewall
Block users from transferring files over FTP.
Microsoft Defender Firewall settings include MdmStore/Global/DisableStatefulFtp, which could be used to disable stateful FTP.
Box 2: Microsoft Defender Exploit Guard
Prevent Microsoft Office applications from launching child processes.
Attack surface reduction rules in the Microsoft Defender.
These rules include: Block all Office applications from creating child processes
Note: Attack surface reduction rule merge behavior is as follows:
Attack surface reduction rules from the following profiles are evaluated for each device the rules apply to:
Devices > Configuration policy > Endpoint protection profile > *Microsoft Defender Exploit Guard* > Attack Surface Reduction
Endpoint security > Attack surface reduction policy > Attack surface reduction rules
Endpoint security > Security baselines > Microsoft Defender for Endpoint Baseline > Attack Surface Reduction Rules.
Reference:
https://docs.microsoft.com/en-us/intune/endpoint-protection-windows-10
Question 3:
You have a Microsoft 365 subscription.
You need to deploy Microsoft 365 Apps for enterprise applications to Windows 10 devices.
What should you do first?
A. From Microsoft Azure Active Directory (Azure AD), create an app registration.
B. From the Endpoint Manager admin center, create an app.
C. From the Endpoint Manager admin center, create an app configuration policy.
D. From the Endpoint Manager admin center, enable Microsoft Store for Business synchronization.
Correct Answer: B
Before you can assign, monitor, configure, or protect apps, you must add them to Intune. One of the available app types is Microsoft 365 apps for Windows 10 devices. By selecting this app type in Intune, you can assign and install Microsoft 365 apps to devices you manage that run Windows 10. Note: Review + create
1. Review the values and settings you entered for the app suite.
2. When you are done, click Create to add the app to Intune.
3. The Overview blade is displayed.
Reference: https://docs.microsoft.com/en-us/mem/intune/apps/apps-add-office365
Question 4:
Your network contains an Active Directory domain. The domain contains member computers that run Windows 8.1 and are enrolled in Microsoft Intune.
You need to identify which computers can be upgraded to Windows 10.
Solution: From Windows on the Devices blade of the Microsoft Endpoint Manager admin center, you create a filter and export the results as a CSV file.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, use the Microsoft Assessment and Planning Toolkit.
The Microsoft Assessment and Planning (MAP) toolkit is something that has been around for a long time, you might have used it to inventory your environment or used it recently to upgrade your desktops to Windows 10.
Note: Microsoft recommends that you use Azure Migrate to simplify your migration process. Azure Migrate provides discovery, assessment, and migration capabilities for applications, infrastructure, and data.
Reference:
https://www.techielass.com/using-maps-azure-readiness/
Question 5:
Your on-premises network contains an Active Directory domain named contoso.com. You perform the following actions:
1. Purchase a new Microsoft 365 subscription.
2. Create a new user named User1.
3. Assign User1 the Security Administrator role.
You need to ensure that User1 can enable Conditional Access policies.
What should User1 do first?
A. Register for Azure Multi-Factor Authentication (MFA).
B. Request the Conditional Access Administrator role.
C. Disable Security defaults.
D. Implement Azure AD Connect.
Correct Answer: C
Microsoft provides security defaults that ensure a basic level of security enabled in tenants that don’t have Azure AD Premium. With Conditional Access, you can create policies that provide the same protection as security defaults, but with
granularity. Conditional Access and security defaults aren’t meant to be combined as creating Conditional Access policies will prevent you from enabling security defaults.
Incorrect:
Not B:
Not required. Global administrator, security administrator, or Conditional Access administrator is enough.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/plan- conditional-access
Question 6:
HOTSPOT
Your network contains an Active Directory domain. Active Directory is synced with Microsoft Azure Active Directory (Azure AD).
There are 500 domain-joined computers that run Windows 10. The computers are joined to Azure AD and enrolled in Microsoft Intune.
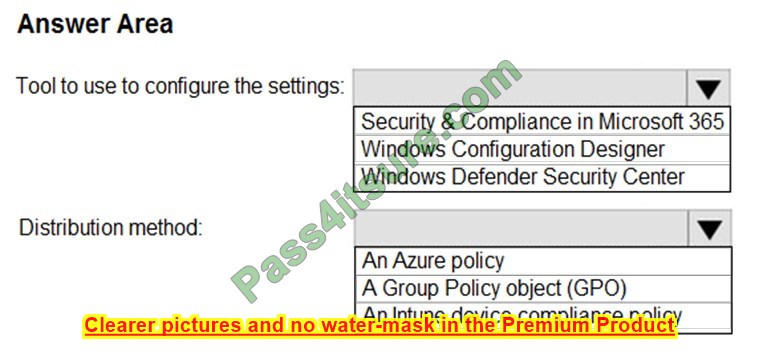
You plan to implement Windows Defender Exploit Guard. You need to create a custom Windows Defender Exploit Guard policy, and then distribute the policy to all the computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
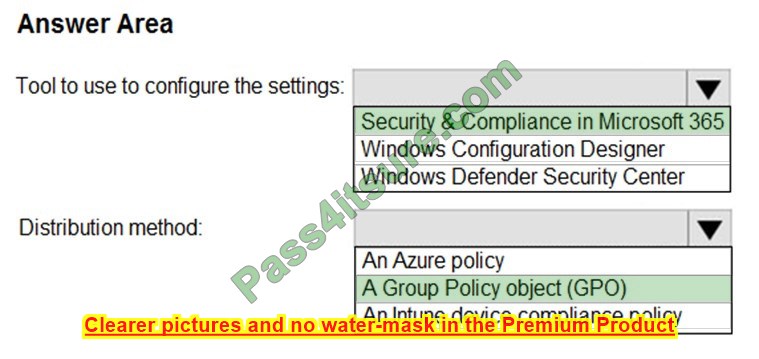
References: https://docs.microsoft.com/en-us/intune/endpoint-protection-windows-10
Question 7:
You are currently making use of the Antimalware Assessment solution in Microsoft Azure Log Analytics.
You have accessed the Protection Status dashboard and found that there is a device that has no real-time protection.
Which of the following could be a reason for this occurring?
A. Windows Defender has been disabled.
B. You need to install the Azure Diagnostic extension.
C. Windows Defender Credential Guard is incorrectly configured.
D. Windows Defender System Guard is incorrectly configured.
Correct Answer: A
Microsoft Defender Antivirus is usually the primary antivirus/antimalware product on your device. To review the protection status
1. On the Antimalware dashboard, you will review the Protection Status blade and click no real-time protection.
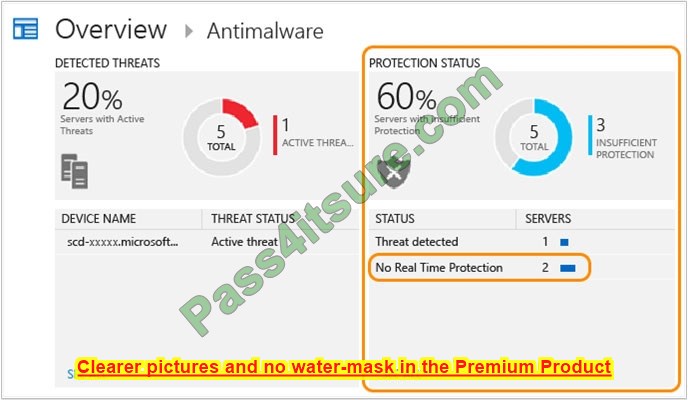
2. Search shows a list of servers without protection.
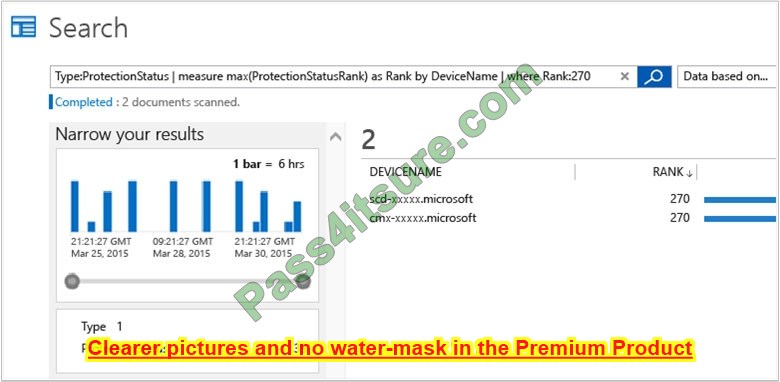
3. At this point you now know what servers do not have real-time protection.
Computers that do not have System Center Endpoint Protection installed (or if SCEP is not detected) will be reported as having no real-time protection.
Reference: https://docs.microsoft.com/ga-ie/azure/security-center/security-center-install-endpoint-protection
Question 8:
DRAG DROP
You have a Microsoft 365 subscription that contains two users named User1 and User2.
You need to ensure that the users can perform the following tasks:
1. User1 must be able to create groups and manage users.
2. User2 must be able to reset passwords for nonadministrative users.
The solution must use the principle of least privilege.
Which role should you assign to each user?
To answer, drag the appropriate roles to the correct users. Each role may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Select and Place:
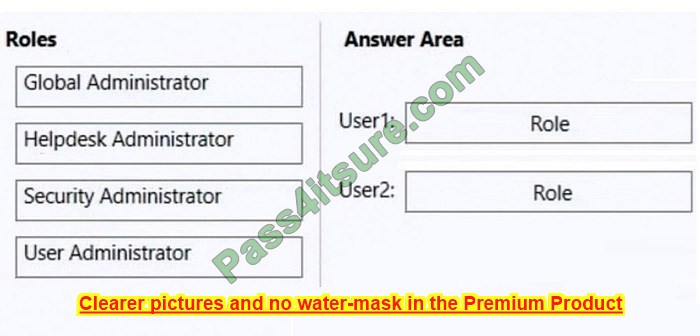
Correct Answer:
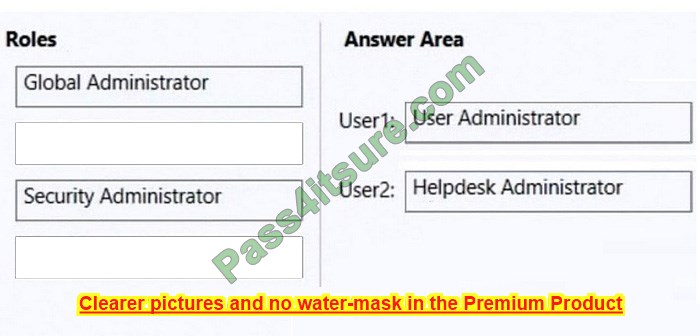
Box 1: User Administrator User admin Assign the user admin role to users who you want to access and manage user password resets and manage users and groups. They can also open and manage support requests to Microsoft support.
Box 2: Helpdesk Administrator Assign the Helpdesk admin role to users who want to reset passwords, and force users to sign out for any security issues. They can also open and manage support requests to Microsoft support.
The Helpdesk admin can only help non-admin users and users assigned these roles: Directory reader, Guest inviter, Helpdesk admin, Message center reader, and Reports reader.
Reference: https://docs.microsoft.com/en-us/microsoft-365/admin/add-users/admin-roles-page
Question 9:
You have a Microsoft 365 subscription.
You need to deploy Microsoft Office 365 ProPlus applications to Windows 10 devices.
What should you do first?
A. From Microsoft Azure Active Directory (Azure AD), create an app registration.
B. From the Device Management admin center, create an app.
C. From the Device Management admin center, create an app configuration policy.
D. From the Device Management admin center, enable Microsoft Store for Business synchronization.
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/mem/intune/apps/apps-add-office365
Question 10:
All the client computers in the forest run Windows 10. Delivery Optimization is enabled.
Your network contains an Active Directory forest. The forest contains a single domain and three sites named Site1, Site2, and Site3. Each site is associated with two subnets. Site1 contains two subnets named SubnetA and SubnetB.
You have a computer named Computer1 that is in SubnetA.
From which hosts will Computer1 download updates?
A. the computers in Site1 only
B. any computer in the domain
C. the computers in SubnetA only
D. any computer on the network
Correct Answer: C
Download mode option: LAN (1=Default)
This default operating mode for Delivery Optimization enables peer sharing on the same network. The Delivery Optimization cloud service finds other clients that connect to the Internet using the same public IP as the target client. These
clients then try to connect to other peers on the same network by using their private subnet IP.
https://docs.microsoft.com/en-us/windows/deployment/update/waas-delivery-optimization-reference
Question 11:
You implement Boundary1 based on the planned changes.
Which devices have a network boundary of 192.168.1.0/24 applied?
A. Device2 only
B. Device3 only
C. Device1, Device2, and Device5 only
D. Device1, Device2, Device3, and Device4 only
Correct Answer: D
Device 5 does not belong to Group 1 or to Group 2.
Note: Deploy a network boundary configuration profile that will have the following settings:
Name: Boundary1 Network boundary: 192.168.1.0/24
Scope tags: Tag1 Assignments:
Included groups: Group1, Group2
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/network-boundary-windows
Question 12:
You need to meet the technical requirements of the IT department.
What should you do first?
A. From the Azure Active Directory blade in the Azure portal, enable Seamless single sign-on.
B. From the Configuration Manager console, add an Intune subscription.
C. From the Azure Active Directory blade in the Azure portal, configure the Mobility (MDM and MAM) settings.
D. From the Microsoft Intune blade in the Azure portal, configure the Windows enrollment settings.
Correct Answer: C
Pilot co-management for the IT department. Configure auto-enrollment of devices to Intune.
1. Sign in to the Azure portal and select Azure Active Directory > Mobility (MDM and MAM) > Microsoft Intune.
2. Configure MDM user scope.
3. Etc.
Reference:
https://docs.microsoft.com/en-us/sccm/comanage/tutorial-co-manage-clients
Question 13:
You are currently making use of the Antimalware Assessment solution in Microsoft Azure Log Analytics.
You have accessed the Protection Status dashboard and found that there is a device that is not reporting.
Which of the following could be a reason for this occurring?
A. Windows Defender System Guard is incorrectly configured.
B. You need to install the Azure Diagnostic extension.
C. Windows Defender Application Guard is incorrectly configured.
D. The Microsoft Malicious Software Removal tool is installed.
Correct Answer: C
References: https://docs.microsoft.com/ga-ie/azure/security-center/security-center-install-endpoint-protection
Question 14:
Your network contains an Active Directory named contoso.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10.
Folder Redirection is configured for a domain user named User1. The AppData\Roaming folder and the Desktop folder are redirected to a network share.
User1 signs in to Computer1 and performs the following tasks:
1. Configures screen saver to start after five minutes of inactivity
2. Modifies the default save location for Microsoft Word
3. Creates a file named File1.docx on the desktop
4. Modifies the desktop background
What will be retained when User1 signs in to Computer2?
A. File1.docx and the desktop background only
B. File1.docx, the screen saver settings, the desktop background, and the default save location for Word
C. File1.docx only
D. File1.docx, the desktop background, and the default save location for Word only
Correct Answer: A
The answer is A for sure!
Desktop background is saved in:
“C:\Users\\AppData\Roaming\Microsoft\Windows\Themes\TranscodedWallpaper”.
Your user profile stores your individual settings under Windows. It is used to re-create your preferred system environment when you log on. This includes everything from your wallpaper and desktop to your email settings and network connections. A roaming profile is stored on a central server which can be accessed from all domain computers.
This allows you to have the same environment settings on every machine to which you log on. Your roaming profile is copied to a machine when you log on and then synchronized back to the server when you log off.
On the KAPLAN exam – The only difference is that in their question there was not a Desktop background change. In their official explanation, they say that the document in the desktop folder surely is retained. The other settings like screen saver, the default save location for Word, and map a network drive (their option instead of our desktop background) are NOT retained.
They explained that the Appdata\Roaming folder stores default templates, some configuration files (like desktop background, and support data. To redirect everything you would have to use a roaming user profile, not Folder Redirection.
So for this scenario, the final answer is A. the file and desktop background.
Question 15:
HOTSPOT
You have a Microsoft 365 E5 tenant that connects to Microsoft Defender for Endpoint.
You have devices enrolled in Microsoft Intune as shown in the following table.
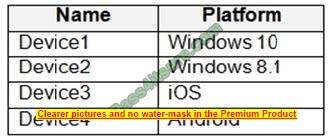
You plan to use risk levels in Microsoft Defender for Endpoint to identify whether a device is compliant. Noncompliant devices must be blocked from accessing corporate resources.
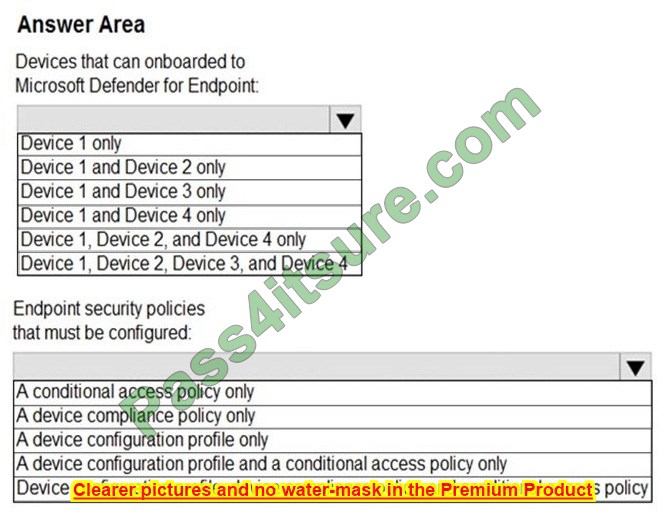
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint, and which Endpoint security policies must be configured.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
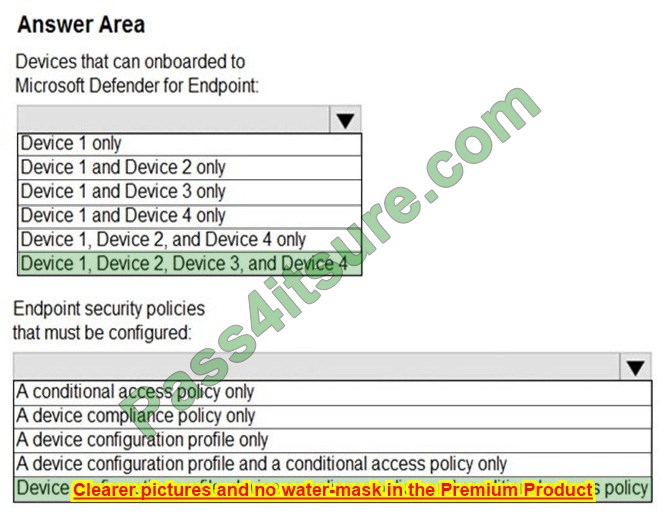
Box 1: Device 1, Device2, Device 3, and Device 4 Supported Windows versions include Windows 8.1 and Windows 10 Other supported operating systems are Android iOS Linux macOS Box 2: Device configuration profile, device compliance policy, and conditional access policy We need all three policies. Establish a service-to-service connection between Intune and Microsoft Defender for Endpoint.
This connection lets Microsoft Defender for Endpoint collect data about machine risk from supported devices you manage with Intune. Use a device configuration profile to onboard devices with Microsoft Defender for Endpoint. You onboard devises to configure them to communicate with Microsoft Defender for Endpoint and to provide data that helps assess their risk level.
Use a device compliance policy to set the level of risk you want to allow. Risk levels are reported by Microsoft Defender for Endpoint. Devices that exceed the allowed risk level are identified as non-compliant. Use a conditional access policy to block users from accessing corporate resources from devices that are non-compliant.
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/minimum-requirements
You can also download the MD-101 exam question PDF (free): https://drive.google.com/file/d/1kBcLVLPJ4ABqVwq-bE16ceGCXG_uYLuo/view?usp=share_link
Conclusion:
Just share it here, about the MD-101 exam. Remember, to pass the MD-101 exam, you need to download the Pass4itSure MD-101 dumps https://www.pass4itsure.com/md-101.html (414 Q&A) to systematically and specifically help you prepare for the exam and be 100% successful.