Successfully passed the EMC DEA-3TT2 exam? Short time? Try the DEA-3TT2 dumps [updated] most impressive DEA-3TT2 study material to help you get through.
The Pass4itSure professional team updated the EMC DEA-3TT2 dumps in 2022 to provide you with 60 real practice questions and answers to complete the Essay – Data Protection and Management Version 2 exam. To go where you want to go, click on the webpage https://www.pass4itsure.com/dea-3tt2.html to get DEA-3TT2 dumps.
What in-depth knowledge do you need for the DEA-3TT2 exam?
DEA-3TT2 exam is a very valuable exam, I have made a summary of the main information as follows:
Full name: Associate – Data Protection and Management
Version 2.0
Code Name: DEA-3TT2
Category: EMC
Certification: DCA-DPM
Certification requirements: Pass the DEA-3TT2 Data Protection and Management Version 2 Exam
You will get:
• Specialist – Technology Architect, Data Protection Version 1.0
• Specialist – Systems Administrator, Avamar Version 9.0
• Specialist – Systems Administrator, PowerProtect DD Version 3.0
• Specialist – Implementation Engineer, Avamar Version 9.0
• Specialist – Implementation Engineer, PowerProtect DD Version 3.0
• Specialist – Implementation Engineer, NetWorker Version 8.0
DEA-3TT2 test time is 90 minutes~ There will be 60 questions, and the passing score will be 60.
How to easily pass the DEA-3TT2 exam?
Choosing the right EMC DCA-DPM Certified DEA-3TT2 learning material(Pass4itSure DEA-3TT2 dumps), or choosing the right DEA-3TT2 question, is the secret.
Why are our DEA-3TT2 study materials more reliable?
Preparing for the DEA-3TT2 exam must have reliable study materials to study and prepare for. We help you strengthen your test preparation with the most accurate and likely EMC DEA-3TT2 questions (according to the latest syllabus).
In addition, we also provide you with free DEA-3TT2 practice questions to try. Practice knowing the truth, come and try.
Take a Free DEA-3TT2 dumps Quiz:
QUESTION # 1
Which are the primary software methods for Data Security Governance?
A. masking, de-identification, and NER
B. masking, classification, and PCRE
C. classification, discovery, and incident management
D. classification, discovery, and de-identification
Correct Answer: D
QUESTION # 2
A consumer performs backup at its on-premise data center for operational recovery. The consumer wants disaster recovery (DR) protection for their data, but they do not want to own and manage a remote site for DR. Which paid backup service is most appropriate for this consumer?
A. Local backup
B. Remote backup
C. Cloud-to-cloud backup
D. Replicated backup
Correct Answer: D
QUESTION # 3
What is the process of identifying and moving inactive data from primary storage systems to lower-cost storage systems for long-term retention?
A. Data archiving
B. Replication
C. Business continuity
D. Data locality
Correct Answer: A
QUESTION # 4
Which data migration involves migrating data at the file level using intermediary compute systems?
A. Host-based migration
B. NAS-based migration
C. SAN-based migration
D. Application migration
Correct Answer: A
QUESTION # 5
Which component of SDDC generates the billing report based on price per unit and number of units consumed for a service?
A. Orchestrator
B. Directory Services
C. Self Service Portal
D. SDDC Controller
Correct Answer: C
QUESTION # 6
An application developer is exploring the best technology to have the application easily transportable and have a small image footprint. Which technology satisfies the request?
A. Containers
B. Traditional application
C. Virtual machines
D. Monolithic application
Correct Answer: A
QUESTION # 7
An administrator is configuring Dell EMC RecoverPoint. Which Dell EMC storage system can be used without a write splitter installed?
A. Unity
B. XtremIO
C. VMAX
D. PowerMax
Correct Answer: A
QUESTION # 8
Which key metric should be used when updating the corporate disaster recovery plan to minimize data loss?
A. MTTR
B. MTBF
C. RPO
D. RTO
Correct Answer: C
QUESTION # 9
Which plane of SDDC is used to perform administrative operations such as configuring a system and changing policies?
A. Management Plane
B. Service Plane
C. Control Pane
D. Data Plane
Correct Answer: C
QUESTION # 10
What are the key functions of data management?
A. detection and orchestration management
B. discovery and operations management
C. configuration and detection management
D. rollout and configuration management
Correct Answer: B
QUESTION # 11
DRAG-DROP
What is the correct sequence of actions during a DDBoost backup?
Select and Place:
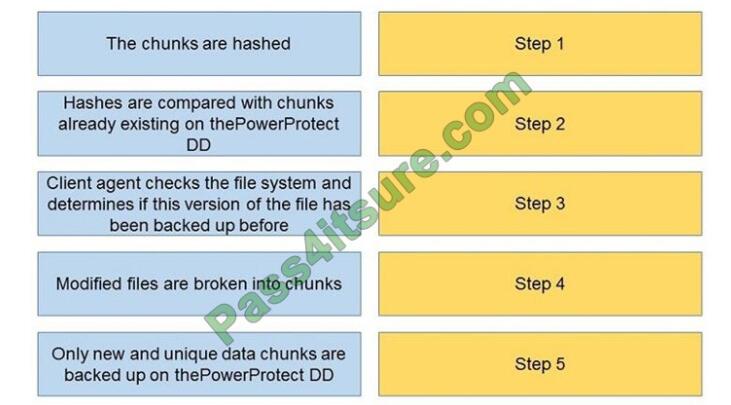
Correct Answer:
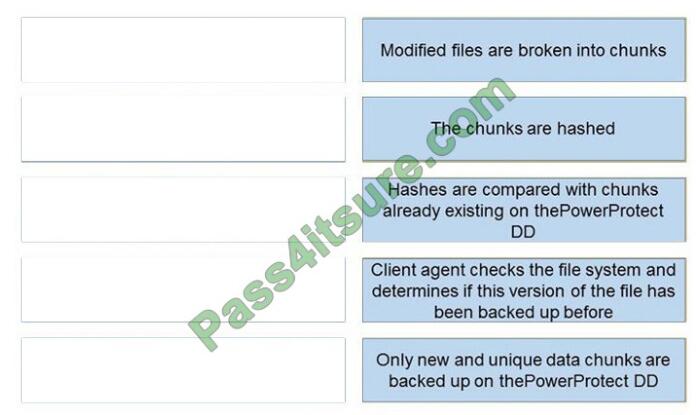
QUESTION # 12
A full backup of a production volume is created on Sunday, and incremental backups are created for the rest of the week. What are the contents of the backup on Thursday?
A. all the data on the production volume
B. all the data that has changed since Wednesday
C. all the data that has changed since Sunday
D. all the data that has changed since Monday
Correct Answer: C
QUESTION # 13
A backup administrator has defined a backup policy where full backups are scheduled at 8 PM every Saturday and differential backups for the rest of the week at the same time. A data loss happened on Friday at 11 AM. How many backup copies are required to restore the requested files?
A. 2
B. 3
C. 6
D. 7
Correct Answer: A
Get the full DEA-3TT2 dumps address: https://www.pass4itsure.com/dea-3tt2.html
Where can I get valid free DEA-3TT2 pdf dumps? Free DEA-3TT2 pdf dumps questions online download: https://drive.google.com/file/d/1ozUhIVZr-PSrVaMh0aHADLZWgkJOcbwN/view?usp=sharing